Your Trusted Partner in Cybersecurity Excellence
Stay One Step Ahead With Cytrusst - The Best Cybersecurity Company To Safeguard Your Digital Assets And Secure Your Future.
Trust the best to secure what matters most and keep your business future-ready
Your Score
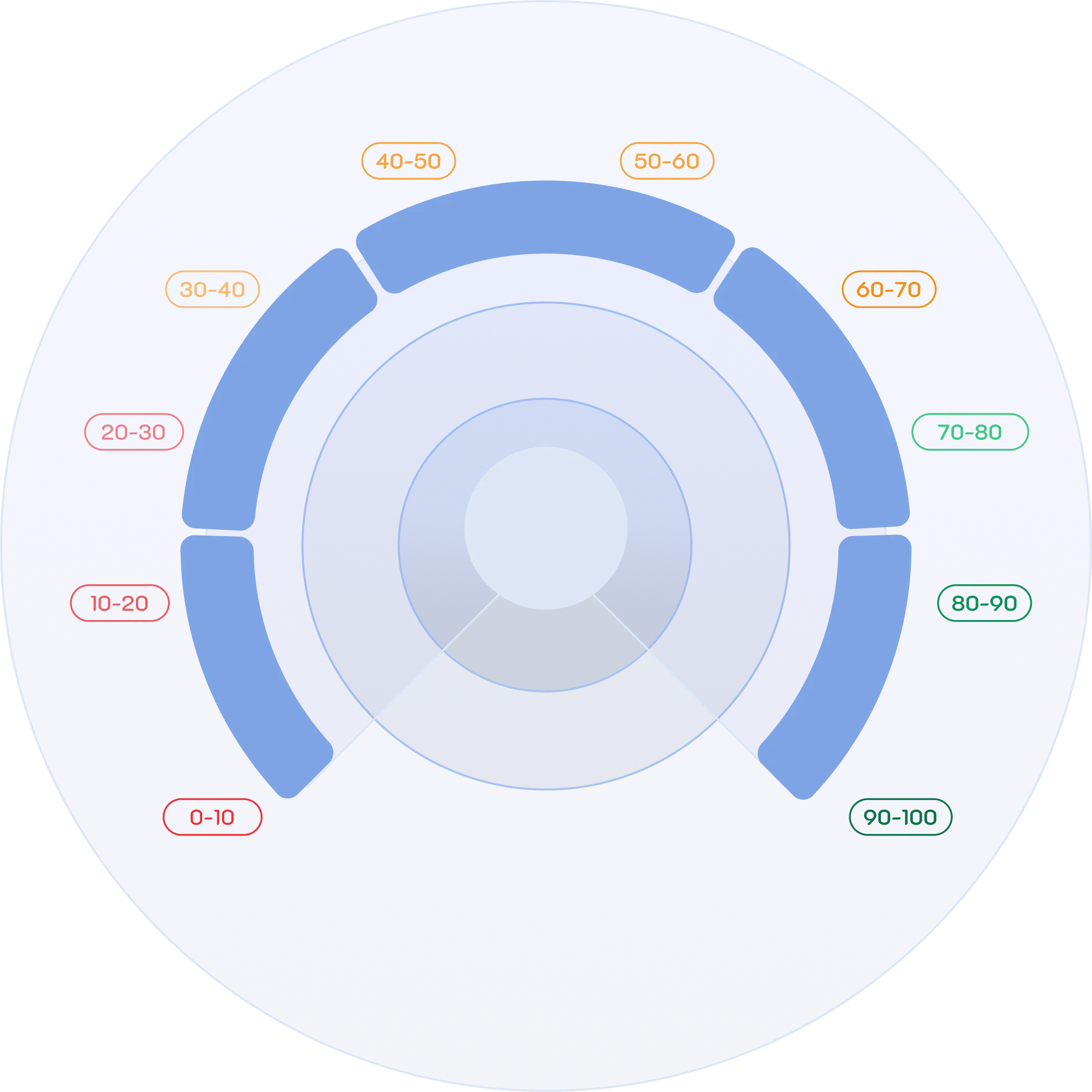
Explore Our Powerful Dashboards and Their Comprehensive Features
Cyber Attack Surface management
Gain complete visibility across your digital landscape. Monitor vulnerabilities in real-time and outpace evolving cyber threats with proactive defence.
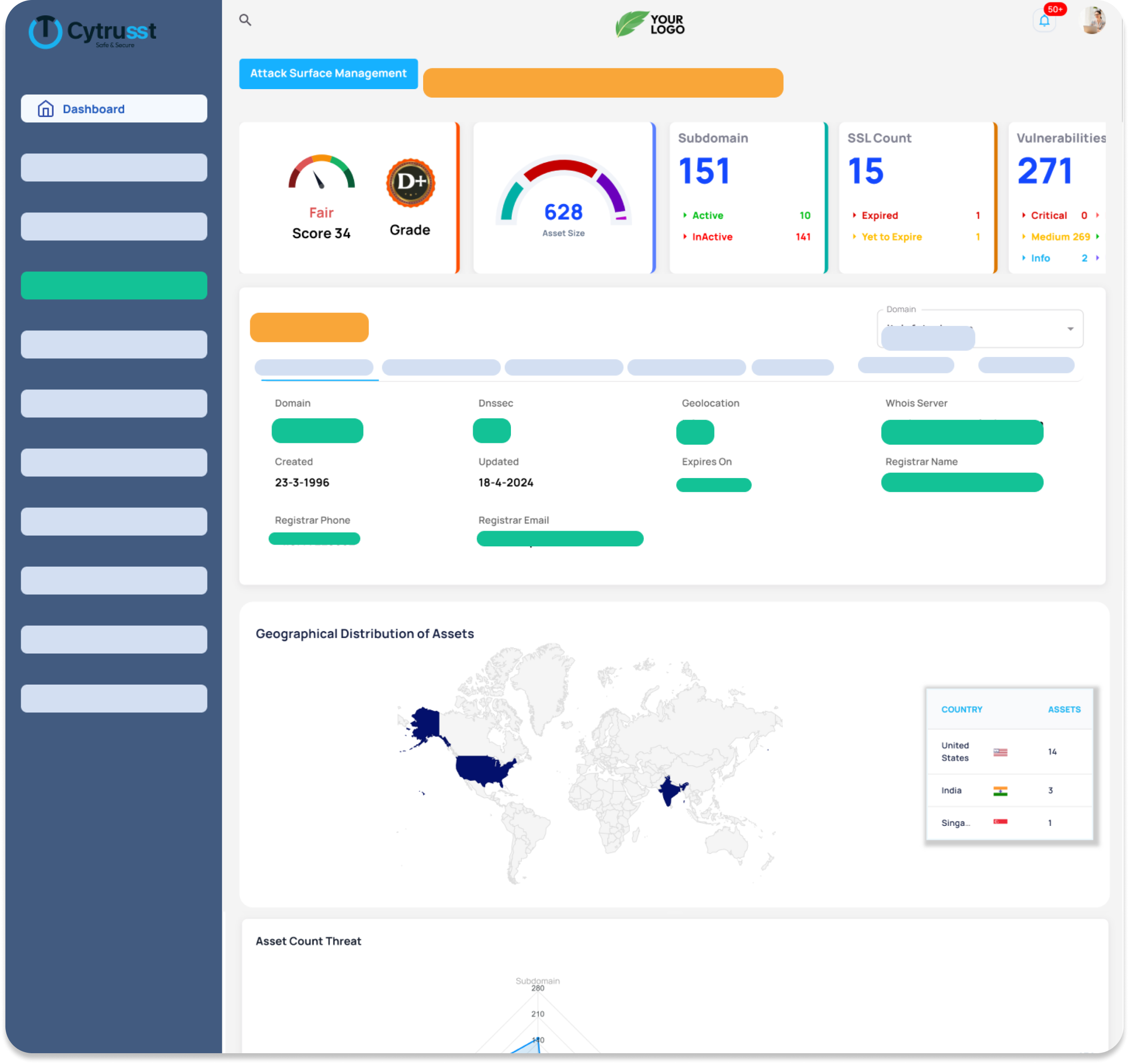
Cloud Security Posture management
Monitor and secure your cloud environment seamlessly. Ensure compliance and reduce risks with instant insights into your cloud posture.

Explore Our Powerful Dashboards and Their Comprehensive Features
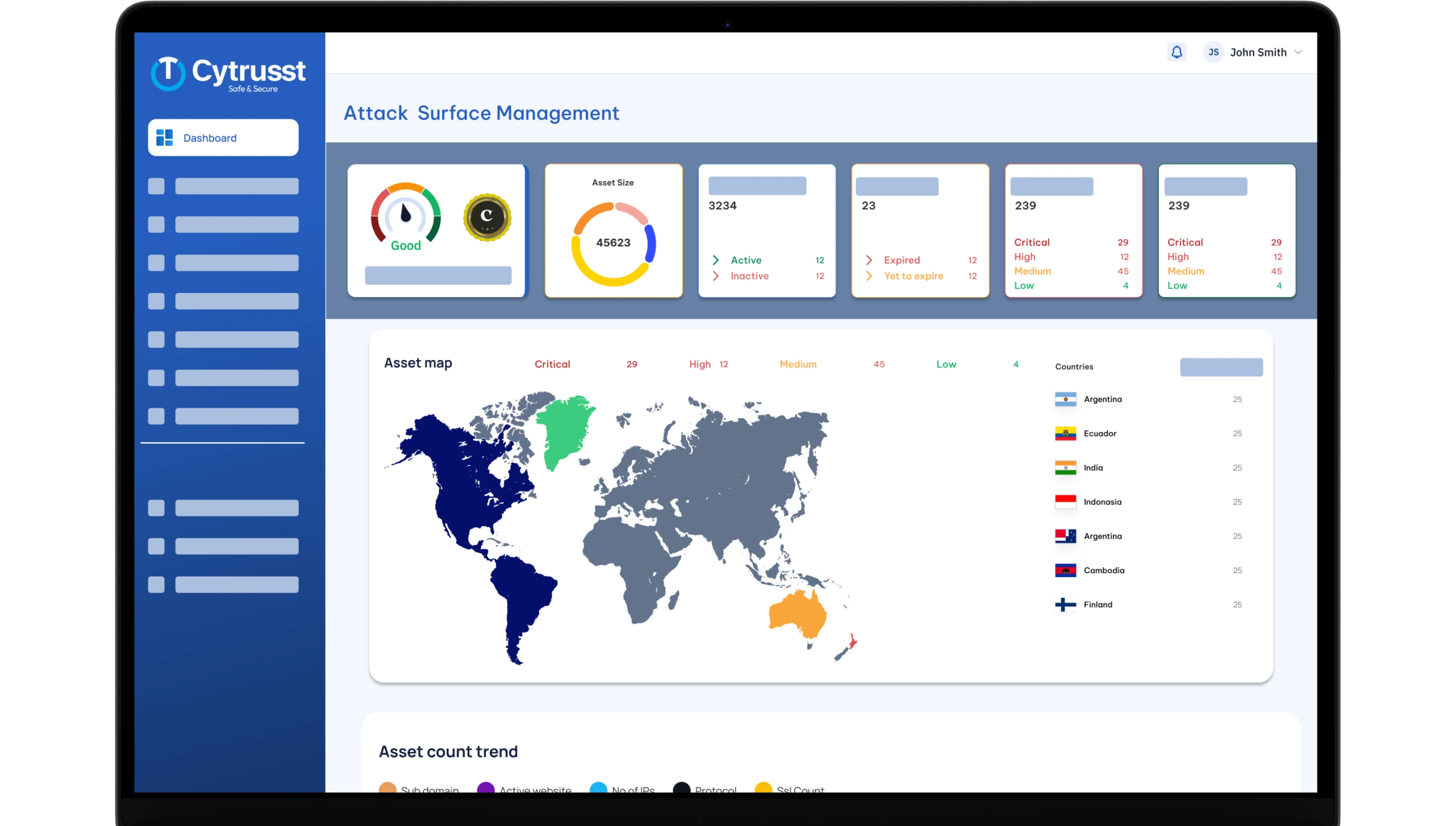
"Cytrusst: Your Trusted Partner in Comprehensive Cybersecurity Solutions"
Best cybersecurity company that helps businesses stay safe online with smart and simple solutions:
Attack Surface Management: Find and fix security gaps in your systems.

GRC: Manage risks and stay compliant with ease.

Third-Party Risk Management: Safely work with vendors and partners

Cloud Security: Keep your cloud data secure and protected.






"The Unified Solution for Trust and Security"
Cytrusst unified platform provides unbeatable Cyber security solution for your multi-cloud environment. As the best cybersecurity company we protect your business from today's most advanced threats.
Enhance Your Platform with Growth-Ready Frameworks
Ensure ongoing compliance with industry-leading security and privacy frameworks such as SOC 2, ISO 27001, HIPAA, PCI DSS, GDPR, NIST, and beyond.

Soc 2
Securely manage customer data by adhering to strict trust service principles like security, confidentiality, and privacy.

UIDAI
Empower every resident with a unique digital identity, unlocking seamless access to services nationwide.

ISO 27001
Framework to build and improve an ISMS, ensuring the confidentiality, and availability of sensitive data while managing risks.

HIPAA
HIPAA safeguards sensitive health information in the U.S., setting standards to ensure privacy, security, and compliance in healthcare.

GDPR
GDPR puts data privacy first, giving individuals greater control and setting new standards for how personal data is handled in Europe.

PCI DSS V4
Enhances payment security, setting strict standards to protect cardholder data and prevent fraud in every transaction.
Securing These Sectors
Information Technology
- Cloud service providers
- SaaS platforms
- DevOps and CI/CD pipelines
- Open-source projects
Logistics
- Cloud service providers
- SaaS platforms
- DevOps and CI/CD pipelines

Banking & Financing
- Stock trading platforms
- SaaS platforms
- Stock Brokerage
Real Estate & Construction
- Property Management Systems (PMS)
- Smart Buildings and IoT
- Real Estate Transactions
- Client and Business Data
Frequently asked questions
Can't find the answer you're looking for? Reach out to our customer support team.
What is Attack Surface Management, and why is it crucial for cyber security?
How does Attack Surface Management differ from traditional cybersecurity measures?
What are the key benefits of implementing Attack Surface Management?
How frequently should Attack Surface Management assessments be conducted?
Can ASM be integrated with other cybersecurity measures?
What is Governance, Risk, and Compliance (GRC), and why is it crucial for cybersecurity?
How does Cytrusst assist in managing cybersecurity risks through GRC?
What compliance standards does Cytrusst GRC support?
Can GRC solutions be customized for different industries?
How often should GRC assessments be conducted?
What are the primary security considerations for moving to the cloud?
How does Cytrusst ensure the security of data stored in the cloud?
Can Cytrusst support multi-cloud environments?
What measures are in place to protect against cloud-based threats?
Is Cytrusst compliant with industry regulations for cloud security?
What is CNAPP, and why is it important?
How does CNAPP differ from traditional security solutions?
What are the key features of a CNAPP?
Key features of a CNAPP include:
- Vulnerability Management: Identifies and mitigates risks in cloud infrastructure, applications, and containers.
- Runtime Threat Detection: Monitors live environments for threats and anomalous behavior.
- Compliance and Governance: Ensures adherence to security standards and regulatory frameworks.
- Shift-Left Security: Integrates security into the development pipeline to detect issues early.
- Unified Visibility: Provides a centralized view of assets, configurations, and risks across multi-cloud environments.
- Infrastructure as Code (IaC) Scanning: Identifies misconfigurations before deployment. Context-Aware Prioritization: Highlights critical risks based on impact and environment context.
Who can benefit from using CNAPP?
CNAPP benefits organizations of all sizes that operate in cloud-native environments, including:
- Enterprises: Ensures robust security for complex, multi-cloud architectures.
- DevOps Teams: Integrates security into development workflows to address issues early.
- Security Teams: Provides centralized visibility and control to manage cloud risks effectively.
- Compliance Officers: Simplifies adherence to regulatory requirements and standards.
- Small and Medium Businesses (SMBs): Offers scalable and cost-effective security for growing cloud environments.
Is CNAPP suitable for multi-cloud or hybrid cloud environments?



