Defending the Unseen:
A Deep Dive into Cyber Attack Surface Management
Empower your organisation with unmatched protection, proactively safeguarding
every step from inception to implementation.
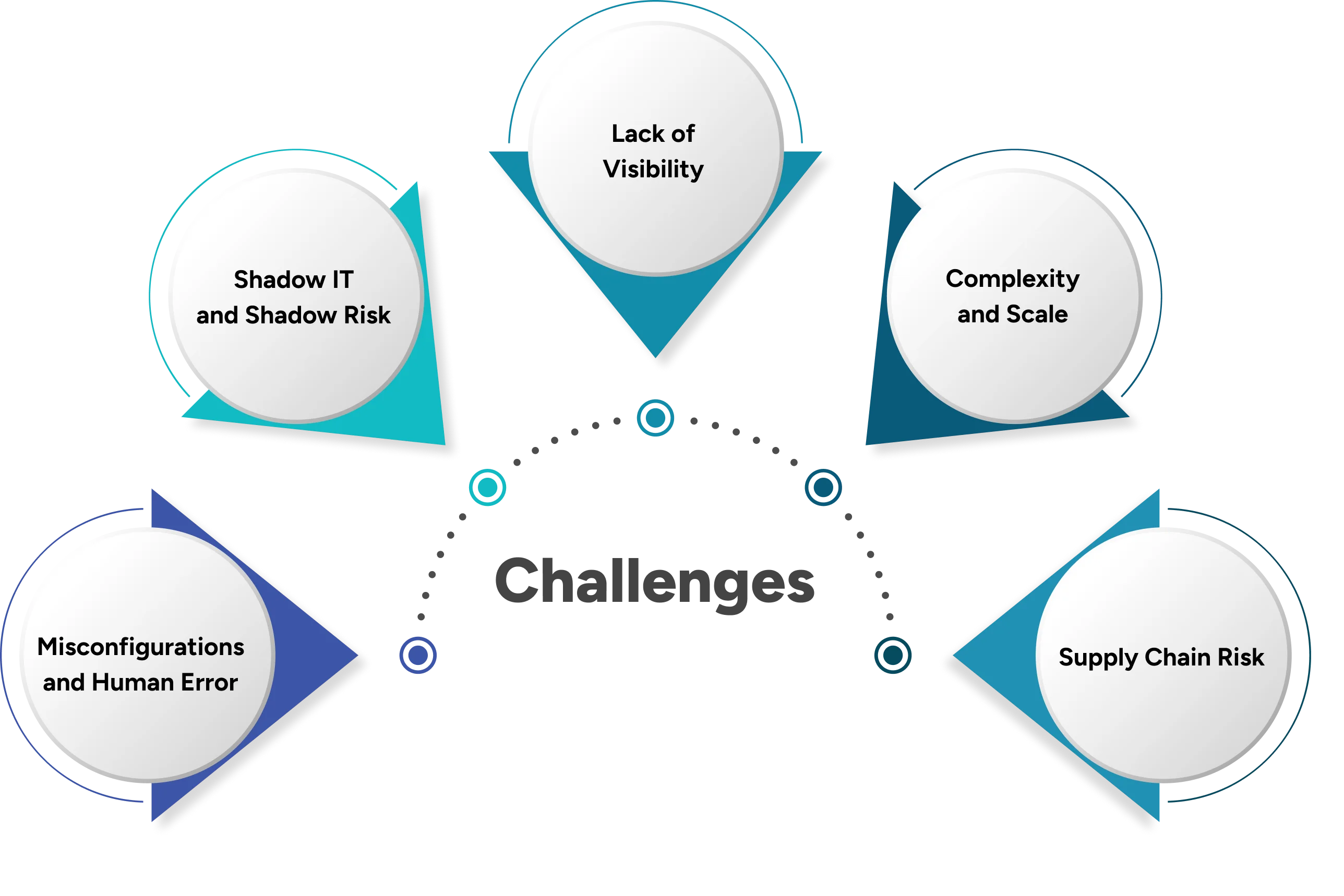
Challenges occurring in
Cyber Attack Surface Management
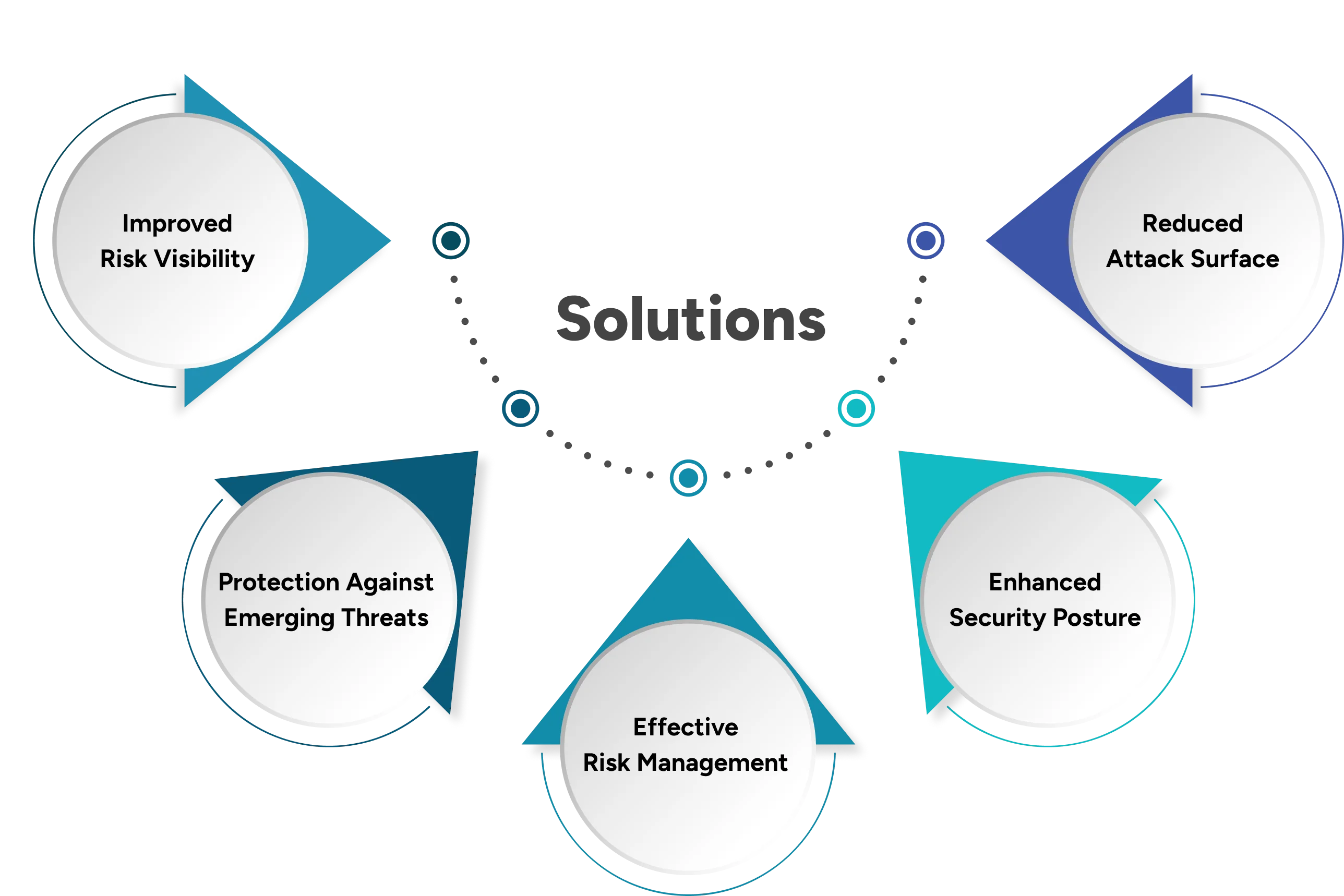
Solutions to solve the challenges occuring in
Cyber Attack Surface Management
Features we have in
Cyber Attack Surface Management
Digital Footprint
A mechanism that automatically lets you find websites and web applications that could potentially belong to your organization. This allows you to decide if these assets need to be covered by your web application security processes.
SSL Certificate
An SSL certificate is a digital certificate that authenticates a website's identity and enables an encrypted connection. If you do not have an SSL Certificate or expired on your website, then all the confidential information on your site might be accessed by hackers. This may lead to leakage of personal data of your customers.
Surface Web
The surface web monitoring can be extracted as the part of the internet that is accessible through a standard web browser like Google or Mozilla Firefox. The content under the surface web can be like exposed secret keys or tokens in organisation GitHub repositories.
LookAlike Domain
Lookalike domains are domains that are found to be visually similar when compared to the domains they are attempting to imitate
Vulnerability
A website vulnerability Is a software code flaw/ bug, system misconfiguration, or some other weakness in the website/ web application or its components and processes. Web application vulnerabilities enable attackers to gain unauthorised access to systems/ processes/ mission- critical assets of the organisation.
Dark Web
Dark Web Monitoring is a service which regularly searches places on the dark web where information is traded and sold, looking for your information Your data's like organisation details, E-mails, Passwords, Personal Details
Brand Monitoring
Brand monitoring is a capability that enables organisations to keep tabs on how their brand is being used online with impersonated profile.Cybersecurity teams implement brand monitoring to gain visibility into mentions of their brands and utilisation of brand assets across the entire public attack surface, including email, social media, domains, app marketplaces, and the surface, deep and dark web.
Threat Feed
Threat Intelligence enables us to make faster, more informed, data-backed security decisions and change their behaviour from reactive to proactive in the fight against threat actors
Mobile Security
Mobile Device Vulnerabilities can put your mobile systems at severe risk with increased intensities. Mobile Application Security try to prevent and bring a solution to Mobile Device Vulnerabilities.has context menu
Email Security
Email security solutions are designed to protect against phishing attacks and other email-borne attack vectors, protecting email accounts from external threats. organisations may need additional solutions to protect against modern cyber threats.
Incident/Report
Cyber security incident reporting captures the details of an incident, such as a new Vulnerabilities or leakage of new Data in Dark web, Email Security and Mobile Security.
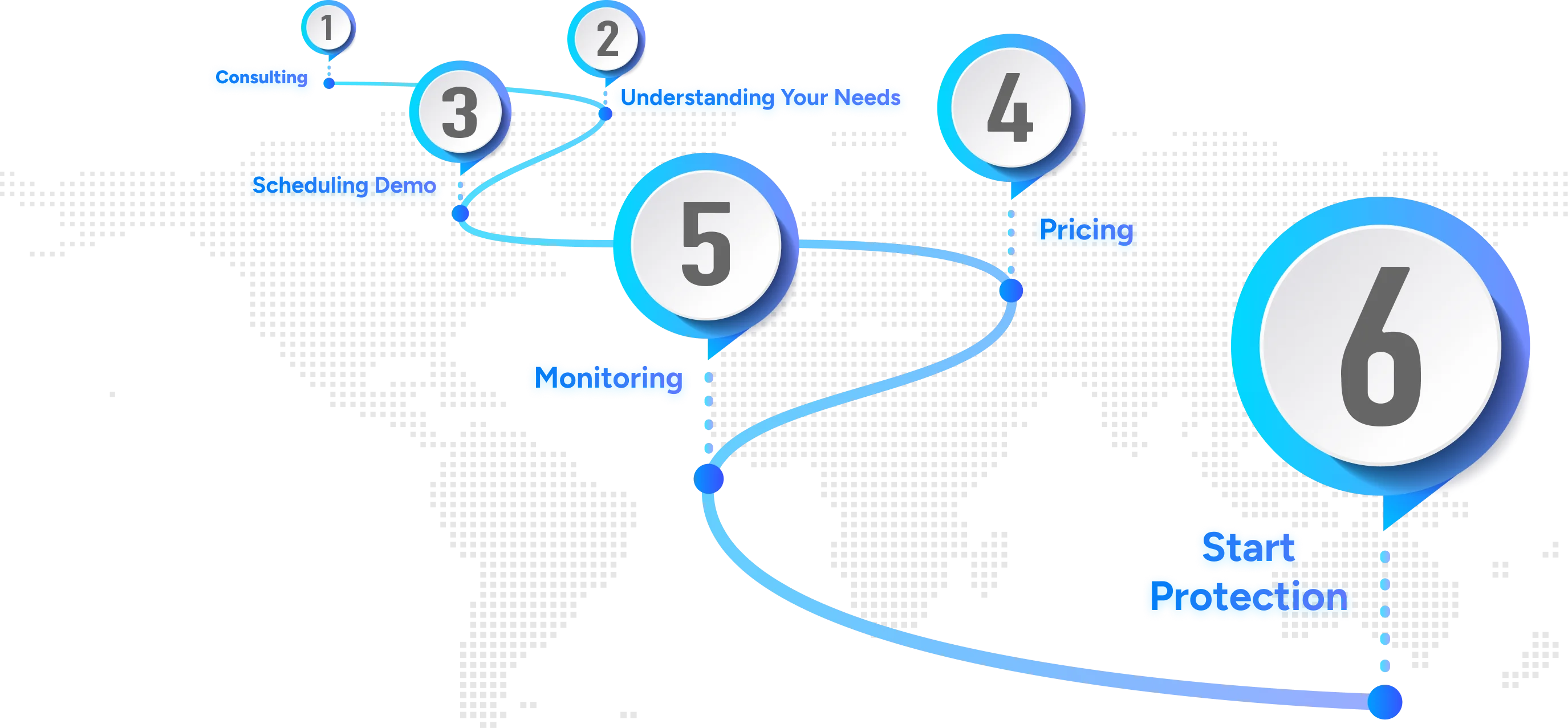
How will be Cytrusst's Approach